How Can We Help?
Personal Banking >>
Achieve your financial goals with the personal service you deserve and the technology you need.
Commercial Banking >>
Build the financial foundation of your business with a Midland operating account.
Wealth Management >>
Financial peace of mind is a conversation away. Let’s connect and take your financial plans to the next level.
Small Business Banking
Partner with a world-class team of relationship managers and a suite of products designed to move your business forward.

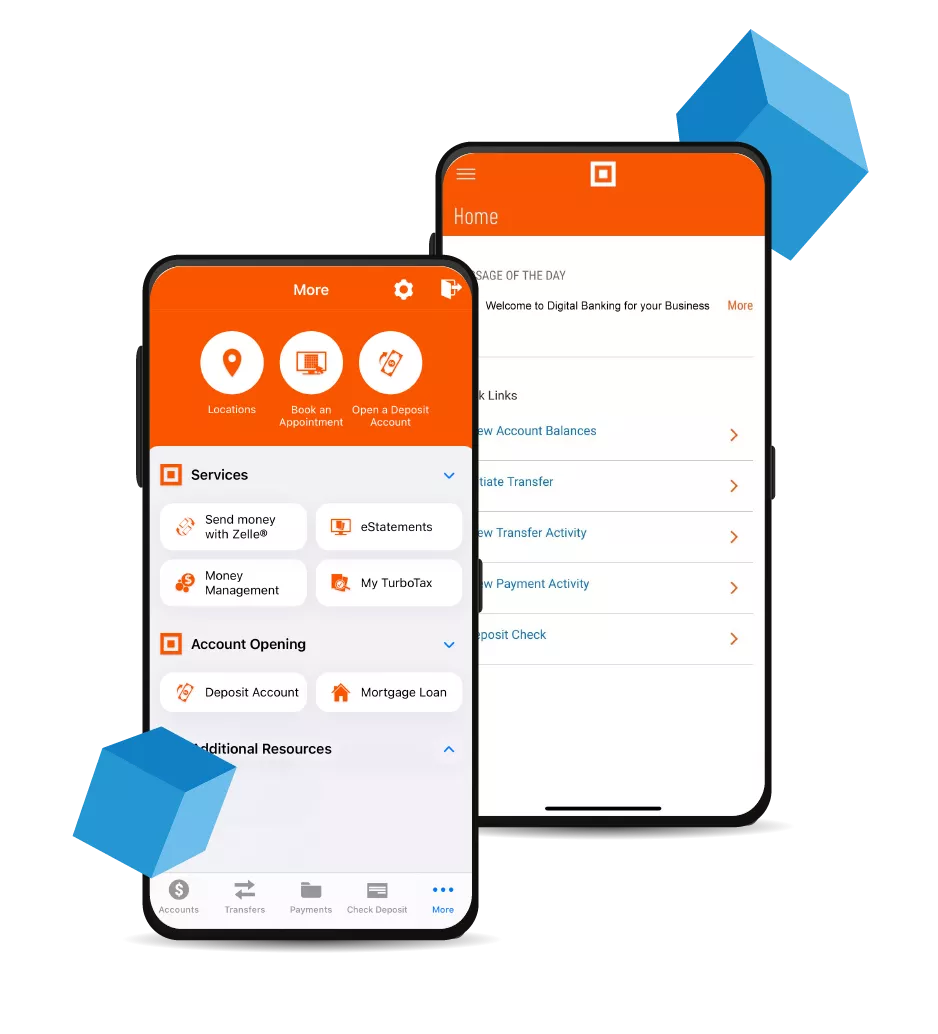
Banking in the Palm of Your Hand
Midland Online & Mobile Features:
- Mobile Wallet
- Mobile Check Deposit
- Money Management Tool
- Smartwatch Banking
- Alexa Voice Banking and more!
Ready For Better Banking?
Open An Account Online
Visit a Nearby Branch
Who We Are
A Little About Us
Established in 1881, we are a strong and growing diversified financial services company, we take heart in providing our clients with world-class service, our shareholders with ownership in a prosperous company, and our employees with a fulfilling career where they can advance.








